
Operating systems are simply tools to do a job…
And therefore, I have to admit that even though I use Microsoft Windows on a daily base to earn my living, I’m also using Linux since almost two decades on various machines. Together with different types of virtualisation I actually do not care whether an OS is running on bare-metal or inside a virtual machine. And given the computing power of recent machines it’s not a question after all anymore. Given this little insight, let’s directly hop into the Ubuntu Jam event from February 2015.
Saturday is usually the time the children are on tour with me and so why not take them to the University of Mauritius and have some fun together. Also, they know quite a number of folks of the Linux User Group of Mauritius, too. When we arrived at the campus it was actually simple to get a proper parking – just speak to the security guys around POWA, they are actually very friendly and willing to help. 😉
Next, we had to look for those Linux geeks and penguins… Near the cafeteria they said, as if I know where the cafeteria is. Frankly, it was on our direct way to ask a group of students. Even though they gave us a strange but curious look, they were really glad to help and we managed to be around in time. Well, even too early… Anyway, enough time to get our gear in place. Even though that my dear son was more busy with his Nintendo DS than a Linux-driven laptop but hey that’s absolutely fine. He’s already geeky enough. Actually, later on – I don’t know he managed it – he was gaming on someone else’s Android smartphone.
Disclaimer: I won’t be accountable for any hacks and root kit installations on your device that he’s going to do!
So better keep your smartphone under your control. Anyway, it seems that the phone owner and my son had a good time checking out some gaming apps. This gave me a bit of liberty to show my older laptop running on Xubuntu 14.10, to answer a couple of Xfce4 related questions and to advertise the Developers Conference. Yes, I keep a git clone on that machine, too – actually running on different TCP ports on Apache and nginx simultaneously. Geeky style…
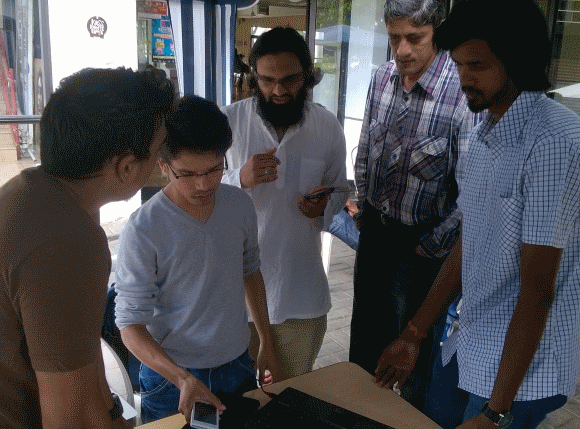
Lots of hardware and software during the Ubuntu Jam – and the choice of tools covered a wide range…

Despite some light spray of rain, we had a great time during the Ubuntu Jam at the University of Mauritius (UoM)
Thanks to the vicinity of the UoM cafeteria it was a no-brainer to just get inside and grab some drinks and food for the lunch-break. Quite surprisingly, they also offer power drinks and other selections. Now, again well fed and still ambitious to handle Linux questions, I managed to get some exchange with Ish, Nirvan, Nadim, Pritvi and others regarding the organisation and ideas for the DevCon. Even though that there was a slight spray of rain, it seems that we all had a good time on the campus and I’m looking forward to attend the next Linux Jam – maybe then on openSUSE Leap or other distributions.






